The Different Network Security Types & Why Your Business Needs Them
Jul 21, 2023

From personal devices to enterprise-level infrastructure, protecting sensitive information and guarding against malicious attacks has never been more critical than in today’s day and age.
“Cyber threats lurk around every virtual corner, waiting to exploit any vulnerability they can find. That’s why investing in robust network security measures is not just an option; it’s a necessity. Our clients entrust us with their sensitive data, and it’s our responsibility to ensure its confidentiality, integrity, and availability,” says Danny Tehrani from Computers Made Easy.
In this article, we will dive into the complex world of all the different types of network security, including:
- Firewalls
- Access controls
- VPNs
- Different types of encryption in network security
- Types of scanning in network security
- And more
Read on to learn more!
What is the Importance of Network Security in Business?
In an interconnected world where the cost of a security breach can far outweigh the investment in preventive measures, network security is a vital investment that no business can afford to overlook.
An increasing number of businesses have taken notice of this in recent years – resulting in the global network security market being valued at USD 53.53 Billion by 2030.
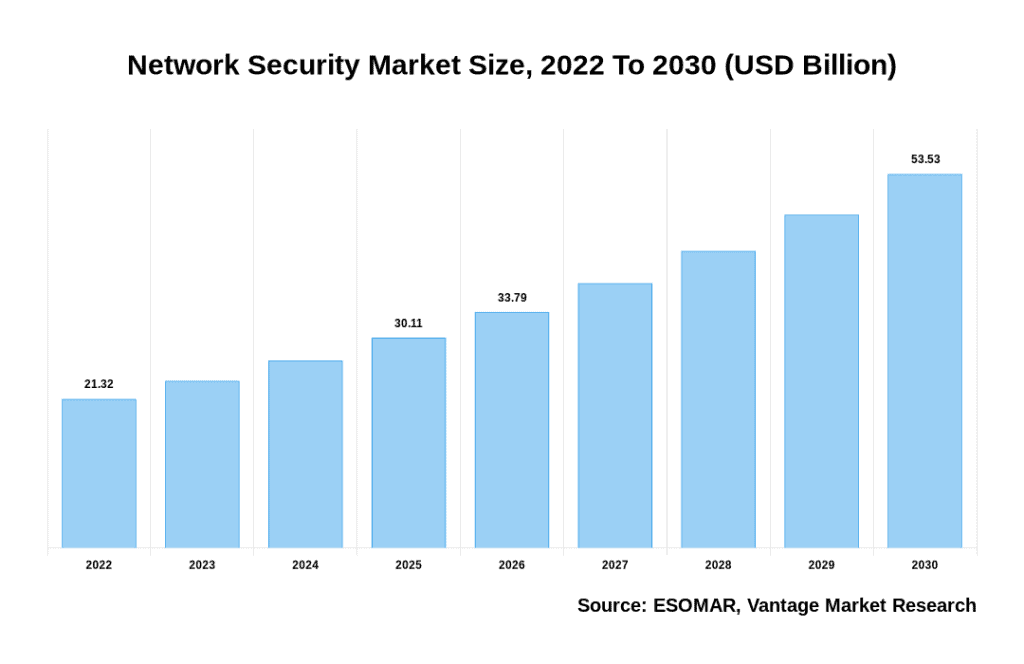
Image Credit: Vantage Market Research.
With cyber threats becoming increasingly sophisticated, the potential consequences of a security breach can be devastating, ranging from financial losses and reputational damage to legal implications. Many of these instances are so severe that they manage to send over 60% of SMBs out of business in just six months of falling victim to a case of cybercrime.
By investing in robust network security solutions, however, you can demonstrate to both your customers and stakeholders your commitment to data privacy, regulatory compliance, and maintaining a competitive edge in a rapidly evolving marketplace.
The Different Types of Network Security: A Closer Look
1. Firewalls
Firewalls act as protective barriers to your network, filtering incoming and outgoing network traffic based on predefined rules. Among the most common network security types, firewalls continuously prevent unauthorized access and keep malicious entities at bay.
Whether hardware- or software-based, firewalls are essential for securing networks, blocking potential threats, and ensuring a safe digital environment.
2. Encryption
Encryption forms the bedrock of secure digital dialogues, working tirelessly to ensure the privacy of your precious business data and shielding it from prying eyes.
Symmetric encryption, which employs a singular key for both encryption and decryption processes, offers an efficient yet speedy encryption method. However, the challenge lies in the safe distribution of the key. Asymmetric encryption, otherwise known as public-key encryption, embraces a different approach, utilizing two distinct keys: encryption and decryption.
Incorporating these encryption methods in your network security measures allows you to fortify sensitive data, preserving the privacy and integrity of your data effectively.
3. Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
Intrusion Detection Systems (IDS) vigilantly scan network traffic, scrutinizing patterns and behaviors to spot anything out of the ordinary.
Picture it as a constant surveillance system, sounding the alarm at the first hint of potential threats. Intrusion Prevention Systems (IPS), however, go one step further. Not only do they detect, but they also actively thwart these threats, delivering real-time protection against malicious intrusions.
When you unite the powers of IDS and IPS, you’re effectively reinforcing your network security, creating a solid defense against the ever-evolving landscape of cyber threats.
Check out these additional resources to learn more about the importance of safeguarding your network with all the different types of network security mentioned in this blog: |
4. Virtual Private Networks (VPNs)
In an era of remote work and global connectivity, VPNs are among the network security types that are crucial for protecting data transmitted over public networks. By establishing encrypted connections, VPNs shield sensitive information from prying eyes, ensuring privacy and confidentiality.
Whether accessing corporate networks or conducting online transactions, VPNs offer a secure tunnel for data transmission, safeguarding against potential breaches.
5. Access Control Systems
Access control is crucial for preventing unauthorized access to networks and resources. Robust authentication mechanisms, such as passwords, biometrics, and multi-factor authentication, verify user identities, granting access only to authorized individuals.
Access control systems also enable organizations to implement role-based access controls, limiting privileges and reducing the risk of internal breaches.
Cost-Effective, High-Quality IT Services Near You: |
6. Network Segmentation
Network segmentation involves dividing a network into smaller, isolated segments, creating barriers against potential attacks. By separating networks based on departments, projects, or security zones, organizations can control access and limit the impact of breaches.
This strategy prevents lateral movement within the network, confining threats and minimizing damage.
7. Endpoint Security
Endpoints, including laptops, mobile devices, and IoT devices, are potential entry points for cyber threats.
Endpoint security solutions, such as antivirus software, encryption tools, and device management systems, secure these devices from malware, data theft, and unauthorized access. This type of network security fortifies the network’s perimeter and ensures comprehensive protection against threats targeting vulnerable endpoints.
8. Network Scanning
There are various types of scanning in network security, including vulnerability scanning, port scanning, and more, which all play a vital role in safeguarding your network. By employing these scanning techniques, your business can easily identify and address vulnerabilities, enhancing overall network security.
9. Employee Education and Awareness
No network security strategy is complete without considering human factors. By 2027, global spending on cybersecurity training will reach $10 billion. Employee education and awareness programs educate users about best practices, social engineering threats, and the importance of data security.
Foster a Culture of Cyber Protection Amongst Your Team
Learn more about our cyber awareness training
Contact UsAt Computers Made Easy, We Make Protection Easy
When safeguarding your network, you need a reliable partner who understands the intricacies of this ever-evolving landscape. That’s where Computers Made Easy comes in.
With 27 years of experience in the industry, we are committed to helping our clients safeguard their networks. Our impeccable track record is reflected in their 100% customer satisfaction rating, a testament to the expertise and trust we have earned over the years.
Choose the trusted experts at Computers Made Easy and experience peace of mind when implementing the different types of network security – contact us now!


