Cybersecurity Assessment Checklist That Puts Your Systems to the Test
Jun 16, 2025

A single missed gap can lead to serious trouble. In 2024, the average cost of a cyber attack for mid-sized businesses rose to $4.88 million. That’s financial loss, brand damage, and legal pressure.
Many organizations invest in security tools but fail to assess existing defenses. Danny Tehrani, CEO at Computers Made Easy, says that “Security practices don’t fail because tools are missing. They fail because businesses never check what’s already in place.”
A well-curated cybersecurity assessment checklist helps you uncover what’s weak, what’s outdated, and what’s missing. It protects you from threats that grow more complex each year.
Let’s see why you need this checklist and what it should address.
Make Cybersecurity Audits Easy and Actionable
Let Computers Made Easy transform your checklist into a powerful tool for genuine compliance, uptime, and peace of mind.
Learn MoreWhy Your Business Needs a Cybersecurity Assessment Checklist
Cyber risks are becoming more sophisticated faster than most small businesses can keep up. With new tech integrations, remote work, and cloud reliance, security environments are growing increasingly complex.
Many organizations don’t realize their current tools or practices are outdated until something breaks. A strong checklist keeps you from making false assumptions about your level of security. It helps you:
- Deal with complex IT setups: Multiple devices, cloud systems, and apps increase your attack surface. A checklist ensures each component is reviewed regularly.
- Identify hidden risks: Many vulnerabilities remain unnoticed because they are not regularly checked. Regular assessments reduce blind spots.
- Stay up to date with regulations: Compliance rules are constantly evolving. The checklist ensures you aren’t falling behind on security requirements tied to your industry.
- Lower your long-term risk: The proper checklist highlights issues early. That helps prevent operational disruptions, financial loss, and external scrutiny.
Without a systematic review, minor errors accumulate. That leads to expensive fixes or worse, targeted attacks.
What Makes a Strong Cybersecurity Assessment Checklist
Not all checklists are built equally. A random template won’t help if it doesn’t align with your actual tech environment and threat exposure.
A high-value checklist must be:
- Focused and itemized: Each checklist item should be specific to a particular tool, system, or policy. This avoids generic reviews and helps assign ownership.
- Tied to user roles: Admins need different controls than end users. Strong checklists organize security needs based on who uses what and how.
- Adaptable: Threats change. So do your tools and your staff. A quality checklist should be reviewed quarterly or whenever systems are updated.
- Business-focused: Every checklist item must be directly connected to risk reduction, operational integrity, or regulatory compliance. If it doesn’t support a measurable outcome, it shouldn’t be there.
A weak checklist just adds tasks. A strong one drives accountability and measurable improvement.
Core Components of an Effective Cybersecurity Assessment Checklist
A complete checklist should cover technical, administrative, and cultural security aspects.
Below are the key areas and what they must include.
Policy and Governance Controls
Start by reviewing your formal documentation. If the policies are outdated or incomplete, the rest of your cybersecurity framework will suffer.
- Review existing security policies for completeness, clarity, and employee alignment
- Verify whether the documentation addresses current threats and operational realities
- Track enforcement. Policies must not only exist, but they need to be followed.
If your policies don’t reflect the way your team works now, they won’t hold up under real threats.
Network Security Evaluation
Most attackers seek out easy network vulnerabilities. That’s why this section is crucial.
- Review firewall settings. Are ports unnecessarily open? Are the rules up to date?
- Test intrusion detection tools. Are logs monitored, and alerts acted on?
- Simulate network-based threats and test your response
A strong network layer limits access to only what’s needed and continuously monitors what’s happening.
| More articles you might like: 7 Risks of BYOD & How to Avoid Them Why Cloud Security Assessments Are Important & How to Perform One Data Migration from Legacy Systems: A Step-by-Step Strategy |
Identity and Access Management
Who can access your systems, and how? If you can’t answer that clearly, you’re already vulnerable.
- Ensure each employee has only the access required for their job
- Run privilege audits: Are former employees still active? Are privileges too broad?
- Enforce MFA across all accounts with sensitive access
Cyber attacks involving stolen or compromised credentials surged 71%year-over-year. Attackers love stolen credentials. Poor access controls hand them the keys.
Data Protection Standards
If you don’t know where your data is, who has access to it, or how it’s protected, you’re at serious risk.
- Follow a cybersecurity risk assessment checklist to map where your sensitive data lives
- Encrypt all sensitive files, both those at rest and in transit
- Set up secure backup and restore procedures for critical business data
Data protection can’t be reactive. It must be automatic and always active.
Endpoint and Device Security
Laptops, mobile phones, and personal devices are now standard. That brings convenience, but also risk.
- Ensure you patch all devices regularly with security updates
- Set clear BYOD rules to define what’s allowed and what security tools must be installed
- Restrict access from unapproved or unmonitored devices
Every endpoint is a potential entry point. If it connects to your systems, you must secure it.
Threat Detection and Monitoring
No matter how strong your perimeter, threats can get through. That’s why internal monitoring matters.
- Deploy SIEM tools that collect, correlate, and alert on suspicious behavior
- Review logs daily for irregular login patterns, privilege escalations, or file access
- Set clear response protocols for alert follow-ups
Detection isn’t just about finding threats; it’s about knowing what to do the moment one is found.
Incident Response and Recovery
You can’t prevent every incident. What matters is how fast and well you respond.
- Maintain a written IR plan that outlines step-by-step actions
- Test your recovery points regularly. Can you restore operations in one hour or one day?
- Include internal and external communication steps in your plan
Strong recovery is about timing, communication, and containment.
Staff Awareness and Security Culture
80% of organizations admit that security awareness training has greatly reduced phishing risks. Most attacks succeed because someone made a mistake. That’s why your team needs to be trained, not just once, but regularly.
- Run ongoing security training programs for all roles
- Test awareness with phishing simulations and report tracking
- Document policy acknowledgment for every new hire and update
Security isn’t just IT’s job. It’s everyone’s job. Your staff must know what to do and why it matters.
How to Use a Cybersecurity Assessment Checklist Effectively
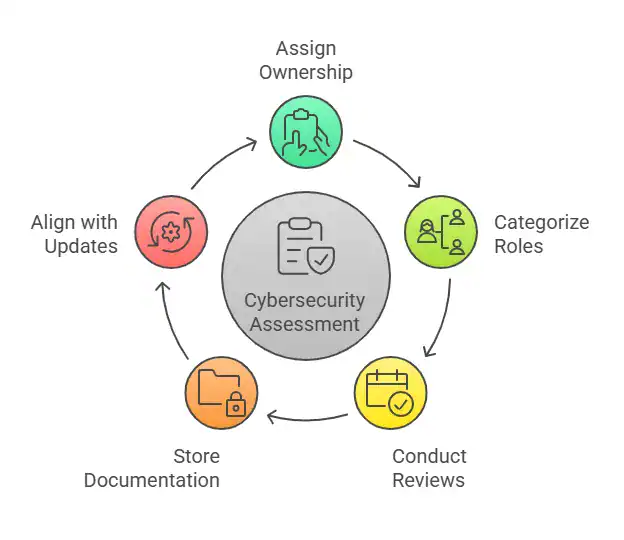
A checklist has no value if it’s not used consistently. You must assign ownership and ensure someone is responsible for updating and executing the review.
- Assign checklist categories to different roles, such as IT, compliance, operations, HR
- Run quarterly reviews and post-incident updates
- Store documentation in a centralized, version-controlled location
- Align checklist reviews with new risks, tools, or compliance updates
Consistency is more important than completeness. It’s better to check 50 items thoroughly than 100 poorly.
How a Cybersecurity Risk Assessment Checklist Saves You Time and Money
Time lost during a security incident is costly. So is the reputational damage that follows.
- Prevent downtime: Early detection of vulnerabilities means fewer outages and smoother recovery
- Avoid brand damage: Fast response and transparency protect your reputation with customers and partners
- Cut legal and response costs: A checklist reduces the odds of large-scale exposure, legal fees, and regulatory fines
- Build vendor trust: Vendors trust organizations that show consistent, documented security practices
Security issues don’t just disrupt operations; they disrupt trust. Checklists help you avoid both.
Checklist Ownership Table
Your team can’t own what isn’t assigned. Here’s a quick reference table to help define responsibility for key checklist areas:
| Checklist Area | Primary Owner | Review Frequency | Notes |
| Policy and Governance | Compliance Officer | Quarterly | Update with legal or industry changes |
| Network Security | Network Admin | Monthly | Test firewall and IDS settings |
| Identity & Access | IT Security Lead | Monthly | Run privilege audits, MFA status checks |
| Data Protection | Data Manager | Monthly | Backup test, encryption config check |
| Endpoint Security | IT Support | Monthly | Patch schedule, BYOD enforcement |
| Threat Monitoring | Security Analyst | Monthly | Log reviews, alert response tests |
| Incident Response | IR Team Lead | Quarterly | Simulation drills, documentation updates |
| Staff Awareness | HR & IT | Bi-Annually | Training records, phishing test reports |
Every item needs an owner, and every owner needs a schedule.
Act Now to Protect Your Business with CME Services
A comprehensive cybersecurity assessment checklist provides structure, visibility, and control. It keeps your team focused, helps you prioritize risks that matter, and supports compliance with evolving standards.
Most importantly, it shows you what’s working and what isn’t, before real issues impact your operations. With the proper checklist in place, you stay ahead of threats, reduce guesswork, and make informed decisions based on facts.
Computer Made Easy has been helping businesses do exactly that for over 27 years, supporting 10,000+ users and 307+ companies across the U.S. We help clients strengthen their defenses while delivering a 99% uptime guarantee to protect both their productivity and reputation.
Reach out to us today and take the first step toward a stronger, smarter cybersecurity program.




