How Effective Information Security Strategies Protect Business Assets and Build Trust
Oct 24, 2025

Cyber threats are advancing quickly, and the pressure to strengthen digital defenses is intensifying. In 2024, 42% of organizations reported phishing or social engineering incidents. This signals that reactive security is no longer a viable security strategy.
Danny Tehrani, CEO at Computers Made Easy, puts it clearly: “Treating information security as an ongoing business process, rather than one-off initiative, is the only way to protect your assets and reputation.”
In this blog, you’ll learn how to assess your current security posture, understand the forces driving today’s risks, and build a strategy that safeguards your organization while strengthening trust with clients and stakeholders.
Secure Every Corner of Your Business
Build a tailored information security strategy that protects your assets and keeps your business agile.
Learn MoreRaising the Stakes: Why Information Security Demands Your Immediate Attention
It may not be obvious, but Information security drives business success. As threats evolve and regulations tighten, a strong information security protocol and timely action protect your assets, reputation, and growth capabilities.
With new threats evolving in both volume and sophistication, leaders must reflect, “Is our strategy built for what’s coming next?”
Here are the forces raising the stakes across every organization:
- Escalating Threats: Cyber incidents are inevitable. Without robust strategies, vulnerabilities become ticking time bombs.
- Regulatory Pressure: Compliance demands are rising. Missteps risk more than fines. They jeopardize reputation and operational continuity.
- Cloud Complexity: 82% of breaches involve cloud-stored data, making cloud security mandatory.
- Talent Gaps: Even with dedicated cybersecurity teams, skill shortages and outdated mindsets leave organizations exposed.
Imagine a ransomware attack hits, and your team discovers outdated protocols and incomplete backups. The impact is business-wide, and every second counts. If the stakes feel high, that’s because they are. Let’s explore how to craft a strategy that keeps you ahead of the curve.
Develop an Effective and Dynamic Information Security Strategy Plan
After a close call with a cyber threat, one thing becomes clear: hoping for the best is not a strategy. You need a dynamic, actionable plan that mirrors your business and outpaces emerging risks.
Despite its importance, compliance alone won’t cut it. Your strategy must be built to outsmart threats and support long-term resilience.
To keep your strategy agile and effective, each step must be clearly defined and consistently executed.
Here’s a quick reference guide:
| Step | Description | Strategy Used |
| 1. Assess Current State | Conduct a comprehensive risk assessment across your digital footprint. | Risk Identification |
| 2. Define Clear Objectives | Set measurable goals aligned with business priorities and compliance. | Goal Setting & Alignment |
| 3. Develop Tailored Policies | Create policies customized to your operational and risk environment. | Policy Customization |
| 4. Implement Layered Controls | Deploy technical, administrative, and physical safeguards. | Defense in Depth |
| 5. Monitor, Test, and Evolve | Continuously monitor, test, and update your strategy. | Continuous Improvement |
Remember: Security is a process, not a milestone. A strategy that evolves with risks ensures your business remains protected, agile, and productive.
Implementing a Zero-Trust Approach for Stronger Protection
Zero-trust architecture has emerged as a cornerstone of modern information security. Gartner reports that 63% of organizations worldwide have adopted it fully or partially. The principle is simple: no user or device should be trusted by default.
Every access request must be verified. Doing this reduces the risk of unauthorized access and potential damage.
A strategic zero-trust rollout starts with understanding your current environment:
- Assessment of Gaps: Audit access controls and identify outdated software that could expose vulnerabilities.
- Continuous Authentication: Require verification for every user and device, every time they attempt access.
- Layered Security Deployment: Combine firewalls, intrusion detection systems, VPNs, endpoint protection, encryption, and network access controls to create multiple defense layers.
- Ongoing Employee Training: Equip staff to recognize suspicious activity and respond effectively, turning your team into active participants in security.
The outcome of integrating these measures is that you can control and monitor access at every level, reducing risk without hindering productivity.
Why An Information Security Strategy Helps Realize Sustainable Growth
A well-built information security strategy is a growth enabler, a trust builder, and a safeguard for everything your business depends on. Here’s how a mature security strategy drives real-world impact:
- Protects Core Assets: Ensures the confidentiality, integrity, and availability of digital resources, shielding sensitive data from leaks and unauthorized access.
- Drives Compliance: Proactive alignment with regulations builds credibility and reduces the risk of penalties or reputational damage.
- Reduces Downtime and Losses: Strategic planning lowers the frequency and cost of breaches, keeping operations stable and revenue intact.
- Builds Stakeholder Confidence: A visible commitment to security earns trust from clients, investors, and internal teams.
Digital trust is foundational. Without it, growth is just an illusion. With it, your business is equipped to scale, adapt, and lead.
| More articles you might like: |
Building a Security-First Culture and Engaged Team
Even the most sophisticated security strategy can falter if your team isn’t aligned with it. Embedding security into your organization’s culture ensures that policies are followed, risks are actively mitigated, and every employee becomes a stakeholder in securing the business.
To strengthen culture and engagement, focus on these foundational steps:
- Leadership Involvement: When executives and managers visibly prioritize security, it becomes clear that data protection is a core business responsibility and not just a concern for the IT team.
- Continuous Training Scenario-based training helps employees recognize and respond to threats in real-world contexts. In fact, 42% of organizations plan to offer cybersecurity certifications to upskill their workforce, boosting both confidence and capability.
- Clear Accountability: Assign ownership for security practices across all levels, from IT teams to end users. Transparent, measurable responsibilities ensure no one assumes “someone else is handling it.”
- Recognition and Feedback: Celebrate proactive behavior and address gaps constructively. When employees see the impact of their actions, they stay motivated to maintain vigilance.
- Integrated Processes: Embed security into daily routines such as password updates, device verification, and secure communication, so it becomes second nature rather than an afterthought.
When you foster a security-first mindset, your employees become an extension of your defenses, spotting suspicious activity, reporting incidents early, and supporting a resilient operational environment.
Assessing Your Security Maturity to Strengthen Your Information Security Strategy
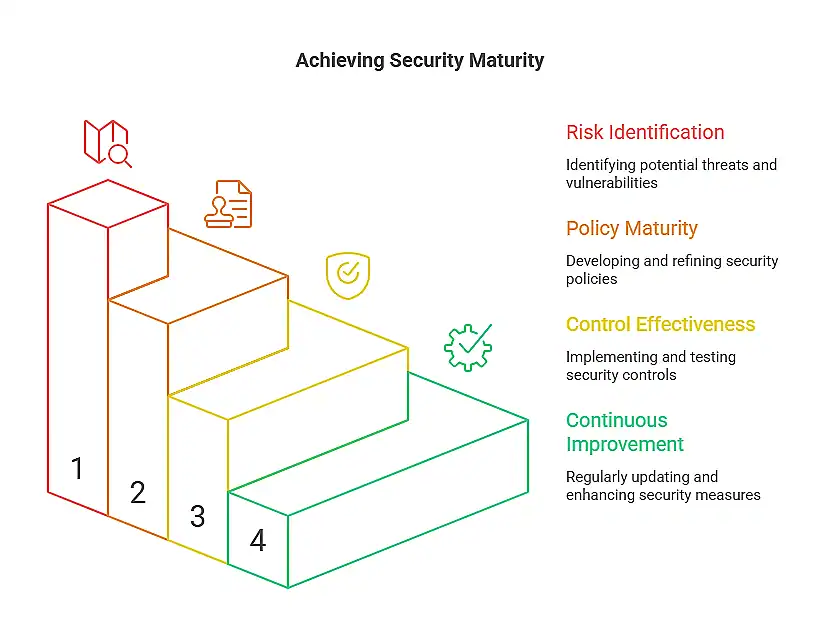
An information security strategy must consistently evolve together with cyber threats, advancing technologies, and shifting organizational priorities. To stay ahead, businesses need visibility.
That’s where security maturity assessments come in.
Evaluating your security maturity provides the insight needed to make informed decisions, close gaps, and continuously improve defenses.
Focus on these key dimensions:
- Risk Identification: Understand your threat landscape and prioritize the most critical risks. This ensures your strategy allocates resources where they deliver the greatest impact.
- Policy Effectiveness: Review whether current policies actively protect your business or need refinement. Mature policies reduce ambiguity and align daily operations with strategic objectives.
- Control Performance: Test both technical and administrative safeguards to confirm they’re not just present, but effective. This helps you fine-tune layered defenses and reinforce zero-trust principles.
- Continuous Improvement: Use real-world incidents, audit findings, and employee feedback to evolve your strategy. Security maturity is a dynamic roadmap for smarter, faster, and more resilient operations.
When you regularly assess these areas, your organization gains clarity on what’s working, where vulnerabilities remain, and how to strengthen both strategy and culture. Measurement becomes the bridge between planning and execution, ensuring your defenses keep pace with the risks ahead.
Field-Tested Information Security Strategies That Keep Threats at Bay
This snapshot highlights strategies different industries use to defend against serious cyber threats and achieve measurable outcomes.
| Industry | Threats Faced | Strategy Used | Results Achieved |
| Finance | Phishing Attacks | Multi-Factor Authentication, staff training, and real-time monitoring | Drop in successful attacks |
| Healthcare | Ransomware | Zero trust model, regular backups, and incident response drills | No data loss, rapid recovery |
| Retail | POS Malware | Network segmentation, endpoint protection, vendor risk management | Contained breach, no downtime |
| Manufacturing | IP Theft | Data classification, encryption, and strict access controls | Protected trade secrets |
Secure Your Business Future with Computers Made Easy
Cybersecurity shouldn’t feel like a hidden fee or an afterthought. At Computers Made Easy, we take a different approach, embedding proactive protection into every managed service contract. No extra charges. No surprises.
Here’s how we help you stay ahead of tomorrow’s threats:
- Full-Spectrum Protection: MDR, EDR, phishing training, and reliable backup come standard, not as optional add-ons.
- Radical Transparency: Clear service levels, zero lock-in contracts, and a dedicated Tier-3 technician who understands your business.
- Reliability Guaranteed: A 99% uptime commitment backed by a 100% money-back guarantee keeps your operations resilient.
With over 500 secured clients and a 98% customer satisfaction rate, we’ve helped organizations build lasting security and confidence.
Contact us today if you’re ready for cybersecurity that’s as forward-thinking as your business. Your future deserves nothing less!




